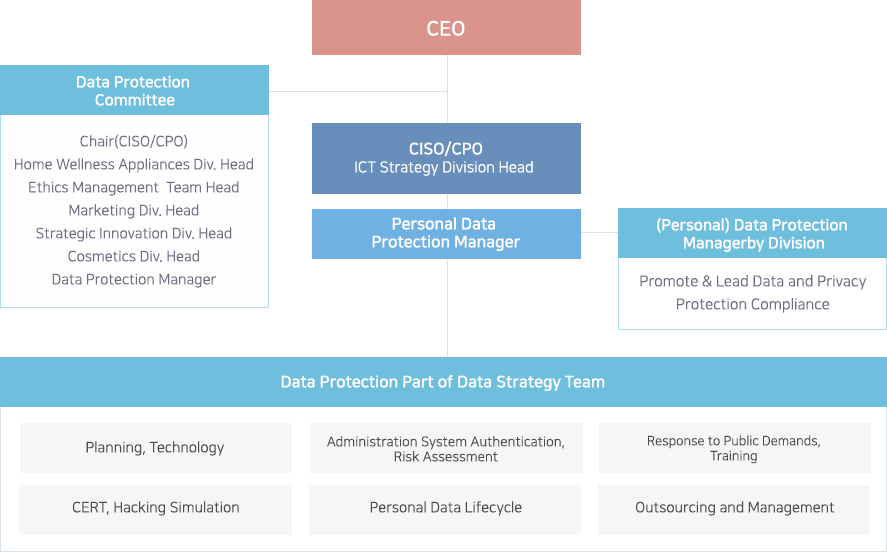
Due to our nature of rental service business, it is important for us to strengthen our data protection system as we collect and handle the personal data of our customers. To this end, we have established a data protection organization with the CPO and ICT Strategy Division playing a central role while improving our service quality by organically integrating product information and analysis service. We also built an integrated management system to improve the efficiency of data protection and management while organizing the Data Protection Committee for the review and resolution of important issues. In 2017, the committee held a meeting once and discussed keeping our data protection policies and guidelines up to date with legislation.

Collect
customer information
Enhance the identification process when signing contracts
Provide option to accept/refuse data collection for marketing purposes

Archive and
use information
Encrypt personal data stored in DB
Encrypt confidential documents in employee PCs

Destroy
customer information
Outsource document destruction process
Require confirmation of data destruction from suppliers
In order to protect our customers’ personal data and information assets, we renewed the ISMS (Information Security Management System) certification and acquired ISO 27001 which is the international standard for managing risks in information security. We also process and monitor customers’ personal data based on the integrated security control system which collects the logs of the entire system using the IDC1).Furthermore, the database encryption and document security system (DRM) helps improve the performance of our security system and protect data from being leaked.
To keep customers’ personal data secure, we ensure that VDI2)is fully implemented and used by the data processors and suppliers. In addition, we identify any vulnerabilities in our sales data system such as web and mobile apps to minimize the exposure of personal data and remove unnecessary information. Furthermore, we organize training sessions against security breaches and IT disaster recovery training sessions once a year to check our security performance and make necessary improvement in our response to security emergency situations.
In order to raise security awareness of our employees, we organize corporate-wide training programs. The programs are sub-divided based on the job and provided both on and offline to improve its effectiveness. In 2017, we focused on our internal security regulations and case studies on documents/personal data security in line with the industrial trend, and ensured every employee completed the training.
| Type | Position | Participants | Completion Rate | Remarks |
|---|---|---|---|---|
| Online Training | Staff-Manager | 4,100 | 100% | Incl. sales, production positions |
| Contractor | 104 | 100% | - | |
| Offline Training | Executive Officers | 22 | 100% | Head of part or higher ranking officer |
| Newly Employed | 38 | 100% | Security training session as part of HR Development Team’s training program |
|
| Experienced | 49 | 100% | ||
| New Coordination Team Manager | 369 | 100% | Security training session as part of Training Team’s training program |
|
| New Staff | 90 | 100% | ||
| New BB* Team Manager | 16 | 100% |
Our security analysis is divided into regular and occasional system analysis sessions while personal data stored in PCs and system access are monitored on a regular basis. In 2017, we conducted a security analysis of personal and public space against 71 teams in our headquarters and any vulnerabilities identified were promptly dealt with on site. In 2018, we will expand its scope to include research labs, sales branches, and manufacturing facilities to identify their regulatory and process compliance while service providers carry out analysis and due diligence based on the contents and scale of service. When it comes to systems such as server and network, we plan to enhance our data security control and deal with vulnerabilities once a year.
| Category | Description | Data Protection Performance in 2017 |
|---|---|---|
| Data Security Management System |
Operation of data security management system |
Continued data security management system control Renewed ISMS certification, acquired ISO27001 for the first time |
| IDC |
Hacking simulation (2 times/year), vulnerability analysis (1 time/year) Security breach response training (1 time/year) |
Increased the target for hacking simulation (app/web) Conducted analysis of system vulnerabilities Increased security breach response training |
| Personal Data, DB |
Encryption of personal data Data control management within DB |
Improved DB encryption level and performance (algorithm) Performed maintenance on SAP data (personal data) |
| PC, Document Security |
Operation of PC security system |
Introduced DRM (document encryption) solution Enhanced the encryption of electronic documents and watermark of printed materials to improve security |
| Employees |
Data security training |
Increased the target for cluster training (offline) Raise security awareness through malware simulation training |